Category: Technology
YouTube Impact – Transforming Viewers into Subscribers and Valuable Leads
YouTube has become a powerful platform that transcends traditional entertainment and marketing channels. Its impact extends beyond mere video consumption, as it offers an unparalleled opportunity to transform viewers into dedicated subscribers and valuable leads. With over 2 billion logged-in monthly users, the platform’s reach is vast, making it an ideal space for businesses and creators to engage their audience. One of the key aspects of YouTube’s transformative power lies in its ability to foster a sense of community. Successful YouTubers develop a unique personality and brand that resonates with their viewers. By consistently delivering high-quality content that aligns with their niche, they create a loyal following that transcends the typical viewer-creator relationship. Subscribing to a channel becomes an act of loyalty, turning viewers into active participants in the content creator’s journey.
Moreover, YouTube’s algorithm plays a pivotal role in guiding viewers towards content they will likely enjoy. By analyzing user behavior and preferences, the algorithm recommends videos that align with viewers’ interests, encouraging them to subscribe to channels that consistently provide content they find valuable. This leads to a positive feedback loop, where increased subscriptions signal to the algorithm that a channel is worth promoting, thereby attracting even more viewers and potential subscribers. The comment section is another potent tool for transforming viewers into valuable leads. It serves as a virtual meeting place where viewers can interact with both the content creator and other fans. This engagement fosters a sense of belonging and it provides content creators with invaluable feedback and insights into their audience’s needs and desires. Responding to comments and addressing viewers’ concerns creates a personal touch that further solidifies the relationship between the audience and the creator, increasing the likelihood of turning viewers into loyal subscribers.
Furthermore, YouTube allows content creators to leverage various features to convert viewers into leads. The use of end screens and cards enables seamless integration of call-to-action buttons that direct viewers to subscribe to the channel or explore related content. These unobtrusive prompts make it easy for interested viewers try this out to take the next step and become subscribers or potential leads. Another powerful tool is the integration of lead magnets into video content. Content creators can offer valuable resources, such as downloadable guides or exclusive access to webinars, in exchange for viewers’ email addresses. This strategy not only increases subscriber counts but also creates a pool of valuable leads for potential marketing initiatives. In conclusion, YouTube’s impact in transforming viewers into subscribers and valuable leads is undeniable. By fostering a sense of community, utilizing the platform’s algorithm to recommend relevant content, encouraging engagement through comments and leveraging various features for call-to-action and lead magnets, content creators and businesses can effectively grow their audience and cultivate a dedicated following. As YouTube continues to evolve, it will remain a vital platform for building meaningful connections with audiences, ultimately leading to increased brand loyalty, conversions and business success.
Concept to Endurance – Role of Shock and Vibe Testing in Product Development
In the dynamic landscape of modern product development, ensuring reliability and durability are paramount to success. From the conceptualization phase to the final product, various stages demand meticulous attention to detail and rigorous testing. Among these essential tests, shock and vibration testing play a pivotal role in guaranteeing a product’s endurance and performance under real-world conditions? The journey of a product from concept to reality is a complex and intricate process. It begins with the initial idea or concept, where designers and engineers brainstorm and create the blueprint of the product. During this phase, the product’s intended usage, environment and targeted performance metrics are established. Herein lies the critical importance of shock and vibration testing – anticipating and assessing how the product will withstand external forces and environmental stresses. Once the concept is solidified, the prototyping phase commences. Physical prototypes are fabricated and undergo rigorous testing to ensure they meet design specifications. Shock and vibration tests are conducted at this stage to identify weak points and vulnerabilities in the product’s structure and components. By simulating real-world conditions, engineers can uncover potential flaws and refine the design for optimal performance and longevity.
As the product takes shape and moves towards production, it undergoes further iterations and improvements. Manufacturers must ensure that the final product maintains its integrity and functionality when subjected to external disturbances. Shock testing assesses the product’s ability to withstand sudden impacts or drops that could occur during transportation, handling or everyday use. Vibration testing, on the other hand, evaluates the product’s resilience to continuous or intermittent vibrations, such as those encountered in industrial settings or transportation environments. The benefits of shock and vibration testing extend beyond merely identifying weaknesses. By subjecting the product to controlled stressors, engineers can also verify and validate its durability and compliance with industry standards and regulations. This ensures that the product not only meets customers’ expectations but also adheres to safety and quality requirements.
Moreover, in today’s highly competitive market, customer satisfaction and brand loyalty are crucial for success. Shock and vibration ats labs testing provide a competitive edge by enhancing a product’s reputation for reliability and robustness. When consumers are confident in a product’s endurance, they are more likely to choose it over its competitors, leading to increased market share and brand loyalty. In conclusion, from concept to endurance, shock and vibration testing form an indispensable part of the product development journey. These tests help uncover weaknesses early in the design process, leading to iterative improvements and a final product that excels in performance and durability. Ensuring a product’s ability to withstand real-world stresses not only enhances its reputation but also fosters customer trust and loyalty. By embracing shock and vibration testing, manufacturers and engineers can create products that not only meet but exceed expectations, setting new standards for quality and reliability in the market.
Protecting Your Digital Investment – Click Fraud Protection Demystified
In the modern digital landscape, businesses heavily rely on online advertising to reach their target audience and drive traffic to their websites. However, as the digital advertising industry grows, so does the threat of click fraud, a deceptive practice that can drain a company’s advertising budget and diminish the effectiveness of their campaigns. To safeguard their digital investments, businesses must employ click fraud protection measures to identify and mitigate fraudulent clicks, ensuring that their advertising efforts yield meaningful results. Click fraud refers to the fraudulent or malicious clicking on online ads with the intent to generate false traffic or exhaust an advertiser’s budget. It can be perpetrated by competitors seeking to deplete a company’s resources, by unethical publishers aiming to boost their revenue or even by bots and automated scripts programmed to mimic human behavior. Click fraud can distort the effectiveness of ad campaigns by inflating click-through rates, reducing conversion rates and wasting valuable marketing funds.
The Road to Resilience – Data Recovery in the Face of Adversity
The road to resilience in the face of adversity is paved with the unwavering determination to recover valuable data. In a world where digital information reigns supreme, the loss of critical data can be a devastating blow to individuals and organizations alike. Whether it is due to natural disasters, cyber-attacks, hardware failures or human error, the need to restore and retrieve data becomes paramount. The journey towards data recovery is not a smooth one; it is fraught with challenges and obstacles that test the limits of perseverance. When disaster strikes, be it a hurricane, earthquake or flood, the immediate priority is ensuring the safety and well-being of individuals. However, once the dust settles, the arduous task of data recovery begins. In such dire circumstances, specialized teams equipped with the latest technologies and expertise embarks on a race against time. These professionals assess the damage, salvage what they can and meticulously reconstruct the digital puzzle. Their commitment to restoring data becomes a beacon of hope as each recovered file represents a small victory in the face of overwhelming loss.
Cyber-attacks pose another formidable threat to data integrity. In an increasingly interconnected world, malicious actors exploit vulnerabilities to gain unauthorized access and wreak havoc on digital systems. When a breach occurs, it is not only data that is compromised, but also trust and confidence. Data recovery becomes an essential part of the recovery process as organizations strive to rebuild their systems and reinforce their defenses. Through forensic analysis, meticulous data reconstruction and stringent security measures, they aim to recover what was lost and emerge stronger in the face of adversity. Hardware failures are an ever-present risk in the realm of data storage. Hard drives crash, servers malfunction and solid-state drives fail unexpectedly. These technical failures can be catastrophic, potentially resulting in the permanent loss of invaluable information. However, data recovery experts employ advanced techniques to salvage data from damaged or malfunctioning devices.
Even human error can lead to data loss, such as accidental deletion or formatting of crucial files. In these instances, the road to resilience begins with acknowledging the mistake and taking immediate action and you could check here https://pierrepirol.com/. Data recovery specialists employ various methods, including file restoration from backups, data forensics and sophisticated software solutions, to retrieve lost information. They understand that mistakes happen, but their unwavering commitment to data recovery ensures that a momentary lapse does not result in permanent consequences. The road to resilience in the face of adversity is a testament to the indomitable human spirit. It is a journey filled with determination, expertise and the relentless pursuit of data recovery. Whether battling the aftermath of natural disasters, combating cyber threats, overcoming hardware failures or rectifying human errors, the goal remains the same: to restore what was lost and emerge stronger than before. In this digital age, the road to resilience is paved with the unwavering resolve to safeguard and recover valuable data, ensuring that adversity does not define our digital legacy.
What is The procedure entry point api-ms-win-crt-runtime-l1-1-0.dll error?
The procedure entry point api-ms-win-crt-runtime-l1-1-0.dll error typically occurs when a program or application is unable to locate or access the required version of the api-ms-win-crt-runtime-l1-1-0.dll file. This error message suggests that the specific function or procedure entry point within the DLL file is missing or incompatible.
Incompatible or Missing Visual C++ Redistributable: The most common cause of this error is an incompatible or missing version of the Microsoft Visual C++ Redistributable package. Some programs rely on specific versions of the redistributable package to function correctly. If the required version is missing or incompatible, the procedure entry point error can occur. To resolve this, try installing the correct version of the Visual C++ Redistributable package associated with the application or program generating the error.
Outdated Windows Operating System: An outdated Windows operating system can also trigger the procedure entry point error. Ensure that your Windows OS is up to date by installing the latest updates and patches provided by Microsoft. Windows updates often include bug fixes, compatibility improvements, and DLL updates that can address issues related to the api-ms-win-crt-runtime-l1-1-0.dll file.
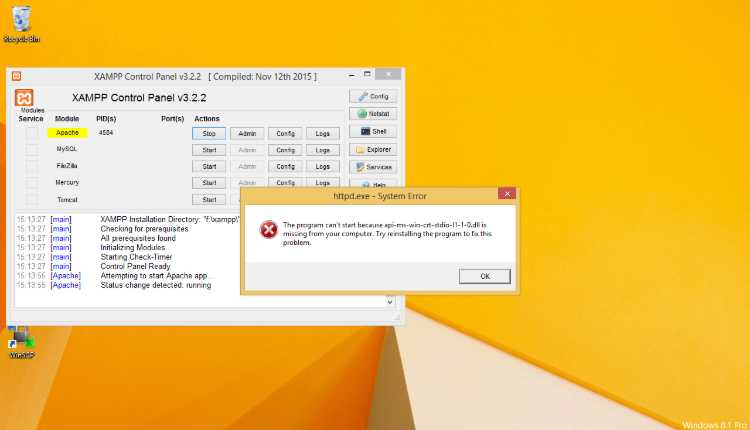
Missing or Corrupted DLL File: If the api-ms-win-crt-runtime-l1-1-0.dll file is missing or corrupted, the procedure entry point error can occur. To resolve this, you can try reinstalling the Microsoft Visual C++ Redistributable package or repairing the existing installation. Uninstall the current package from the Control Panel and then download and install the latest version from the Microsoft website. Additionally, running a system file check using the SFC System File Check tool can help detect and repair any corrupted system files, including the api-ms-win-crt-runtime-l1-1-0.dll file.
Compatibility Issues: Compatibility issues between the application or program and the installed version of the Visual C++ Redistributable package can trigger the error. Ensure that the application or program is compatible with the version of the redistributable package you have installed. Check the application’s documentation or contact the software developer for information on the required version of the Visual C++ Redistributable package.
Malware or Security Software Interference: Malware infections or certain security software can interfere with DLL files, including the api-ms-win-crt-runtime-l1-1-0.dll file. Perform a thorough scan of your system using reliable antivirus or anti-malware software to detect and remove any potential threats. Additionally, temporarily disable or adjust the settings of your security software to check if it is causing the error.
Seek Professional Help: If the above solutions do not resolve the procedure entry point error, it may be necessary to seek assistance from a qualified technician or contact the software developer’s support team. They can provide more specific guidance and troubleshooting steps tailored to your system and the application generating the error.
Resolving the procedure entry point api-ms-win-crt-runtime-l1-1-0.dll error involves ensuring the compatibility of the Visual C++ Redistributable package, updating the Windows operating system, repairing or reinstalling the DLL file, checking for malware infections, and seeking professional assistance if needed.
How Does Hiring Voice ID Forensics Service Is Advantageous For Everyone
The topic of a number of achievement Television demonstrates like Criminal Brain, Law and Buy together with CSI, forensic science rapidly catches the eye of various men and women due to a number of interesting aspects and surgical procedures. Also, it provides an incredibly substantial position in local community, specifically regarding unsolved and unexplainable situations. Let’s have a look at its significance and also other fascinating factors behind it.
Significance
In line with the thesaurus, forensic voice analysis works jointly with the treatment of recognizing, discovering, individualizing and interpreting actual evidence. Afterward, the real key regions of medication and science is going to be utilized to treatment this kind of evidence for your purpose of civil law and criminal supervision. It employs distinct technological disciplines like science, chemistry and biology. Add to that, furthermore, it takes into account other vital areas like mindset, geology as well as PC science. Each and every crime case is searched thoughts, remnants of muscle tissue and substances. Other key components to take into account are materials and stuff kept on the industry inside the crime.
Looking at Biological Traces
Biological remnants take part in a very huge portion in this significant discipline of science. Suspects, long lasting patients as well as the deceased person are searched for all-substantial remnants, which might actually assist in the successful dealing with of criminal acts. The audio forensic specialists track consist of semen, go of your hair and blood flow, which are generally beneficial in getting rid of DNA that is usually to be useful for comparison analysis. DNA is significantly crucial in working with odd circumstances mainly because it can certainly help recognize people, even folks in whose express are over id. Locks, fingernails or toenails and skin pores and pores and skin are great types of DNA. Also, biting periodontal range, cig butts and bloodstains are one of the most well-known biological remnants.
Considering Substance Remnants
Quantitative analyses are performed on chemical substance materials to aid fix criminal offenses. Soil test trial samples, fabric and gunshot residues can help a lot in forensics. Furthermore, forensic researchers could also evaluate blaze grime, paints and drugs. To assist you to solve fireplace-related criminal offenses and conditions, it really is exceptional to take into account different types of elements for example gasoline and kerosene.
Studying Actual Evidence
As well as product traces and biological remains, it happens to be more important to check out every one of the accessible real actual evidence. Handprints, footprints and fingerprints are part of this category. Moreover, source of information markings, reduced locations and wheel locations can also be extremely helpful in forensics.
For More Information and also other Significant Information
When checking biological trial run examples, the most important strategy is polymerase series effect. Next, the final results will undertake gel electrophoresis. Other valuable techniques in forensics entail liquefied chromatography, gas chromatography and solid-routine little-removal. Forensics has a variety of subdivisions like digital forensics, criminalistics and computational forensics. Other considerable career job areas include forensic DNA analysis, forensic archaeology and forensic anthropology.
Access the Dark Web – Way to Find A Comprehensive Overview
The dark web, also known as the darknet, is a hidden part of the internet that is not indexed by standard search engines. It is estimated to be about 500 times larger than the surface web, which is the portion of the internet that is accessible through standard search engines. The dark web is accessed through specialized software that provides anonymity to users, making it a popular destination for criminal activity. Accessing the dark web requires the use of a special browser, such as Tor or I2P, which is designed to keep a user’s identity anonymous. These browsers work by routing internet traffic through a series of servers, which makes it difficult to trace the origin of the traffic. While these browsers can be used for legitimate purposes, they are often used by criminals to conduct illegal activities such as drug sales, hacking, and money laundering. One of the most popular ways to access the dark web is through Tor, which stands for The Onion Router. Tor is free and open-source software that allows users to browse the internet anonymously. It works by encrypting a user’s internet traffic and then routing it through a series of servers, which are operated by volunteers around the world.

Each server in the chain only knows the identity of the server that it received the traffic from and the server that it is sending the traffic to, which makes it difficult to trace the traffic back to its origin. To access the dark web using Tor, a user must first download and install the Tor browser. The user can then navigate to a website that uses the .onion domain, which is only accessible through Tor. These websites are often used for illegal activities, such as drug sales, weapons trafficking, and child pornography. However, there are also legitimate websites that can only be accessed through the dark web, such as whistleblower sites and forums for political dissidents. Another way to access the dark web is through I2P, which stands for Invisible Internet Project. I2P is similar to Tor in that it provides anonymity to users, but it is designed to be more decentralized and resilient to attacks. I2P uses a network of peers to route internet traffic, which makes it more difficult for law enforcement to disrupt the network.
The dark web is not a safe place, and users should take precautions to protect their identity and their devices. Users should never give out personal information or download files from unknown sources. They should also use strong passwords and two-factor authentication whenever possible. Finally, users should be aware that law enforcement agencies around the world are actively monitoring the dark web and are working to identify and prosecute criminals who use it. In conclusion, the dark web is a hidden part of the internet that is accessed through specialized software that provides anonymity to users. While it can be used for hidden wiki legitimate purposes, such as protecting the anonymity of whistleblowers or political dissidents, it is primarily associated with illegal activities. Accessing the dark web requires the use of a special browser, such as Tor or I2P, which is designed to keep a user’s identity anonymous.
Circle Recovery – The Stipends as a whole and Limitations
Circle recovery is normally not looked at until you are faced head on with the troublesome that by and large includes getting one or even all of your business archives brought back. we have at one time been in the very same situation and the reality of the situation is most PC owners have expected to recover PC records using a sort of plate recovery contraption ultimately.

Precisely what not to endeavor to do
Every PC bought joins a recovery Disc. Numerous natural individuals acknowledge this can be a good PC data rescue programming program. You should recall that this specific plate will reestablish your fundamental PC plans. In any case, the application cannot get back any kind of additional program and moreover data that you have had on your own PC not long after you acquired it. Another manner by which to express every single digit of it is if you use the recovery program rather than plate recovery applications, you basically will achieve deleting or annihilating every single program that did not come presented in your PC system. You will similarly lose any of your PC data that you have arranged on your own PC or PC. Which suggests that in the event you do not as of now have a sufficient back up of this data that you might have arranged in your PC system, everything would remain eradicated forever if you do not recover it going before once again introducing the PC to its basic decisions.
The plate recovery task
If you really have a situation that hard circle drive rescue PC undertakings will understand, the task before you is not generally so irksome as you may perhaps think. Different devices will be so obvious to work with that basically all you ought to complete is put in the moderate plate or a floppy would it be a good idea for you routinely approach one, use the PC data recovery programming move by move and after that add another USB hard circle for you to recover your chronicles to a safeguarded sparkling clean hard drive. When finished, you might work with the PC producer’s Cyber Security recovery circle so you can reload your functioning structure and presently copy the recovered reports to your as of late reestablished PC or PC. To be sure, hard circle drive data record recovery might take a pattern of time. Likewise, clearly, you will find it is not almost basically as connecting as a lot of elective endeavors you would probably prefer end up doing. Notwithstanding, you are getting your PC data back before long when it is fruitful.
Cheap Windows Lease – Guess What You Really want To Be Aware?
Have you anytime expected to reinstall Microsoft Windows 11 yet have been not ready to find the product key? The Windows 11 key is for the most part arranged on a yellow sticker on the back of your PC, or on the base, if you own a PC. Once in a while, the sticker will be arranged inside the Compact disc sleeve of your product, or in the product manual. In any case, if for some mysterious reason you cannot find the product key, you lose a huge programming license. You may moreover lose a ton of time endeavoring to pursue the key down, or examining different PC conversations for a response. You may be allured to by another copy of Windows 11, instead of going through the issue of finding another Windows 11 Key. Nevertheless, the Windows 11 key may truly be arranged on your PC. During the establishment association, the Windows 11 course of action program prompts you for your product key. Since it is currently clear to such an extent that your product key is mixed on your PC, you simply have to know how to unscramble it, or how to get a replacement product key.

The strategy you pick depends upon your situation. Using a utility to unscramble it is generally speedy and basic. In any case, expecting you have a special Disc from Microsoft, you could notice it better to directly contact Microsoft. The advantage of using a product utility to find your Windows 11 key is that it will in general be done quickly and check here http://newforestpony.net/2023/how-to-get-a-genuine-windows-11-key-at-an-affordable-price.htm. Typically, the utilities are minimal in size and can be downloaded and introduced in a little while. You would not have to hold on, or pay for, client care at Microsoft, and you could save the utility and save it for in a little while. Most keyfinder utilities go with a limit that licenses you to save your Windows 11 Key to a record, so you can keep it in a safeguarded spot and at definitely no point lose it later on.
Download a Keyfinder utility. These can be found by doing a Google search for product key or Windows 11 key. Introduce the utility by complying with the onscreen bearings. The utility ranges your system and introductions the product key If you would not worry keeping it together some time for client support, you could need to contact Microsoft for a key. In any case you can use this decision if you have the main Windows 11 establishment Cd. Tell the specialist you need another product key. The representative should know a code on your special establishment plate and will give you another key. As of now, you want to a pristine Windows 11 tablet or even a Windows 11 PC they could really be both in one, but imagine having to re-introduce your applications in general, changing the settings to how you really want them especially like on your other PC, etc.
Essential Capabilities for a Team Developer in Management
Regardless of what your working environment is whether an expert worldwide, or a neighborhood sports club, you will hear the words team building, team player, my team, more than frequently, yet a small bunch of them figures out how to comprehend the guiding principle of making an encounter of teamwork. A team is few individuals with integral abilities who are focused on a typical reason, execution objectives, and approach for which they consider themselves responsible together.
- What is the center importance of being in a team?
Being in a team is a consequence of being a piece of an option that could be bigger than you. It provides you with a feeling of having a place with a specific gathering, a gathering that you work with and for. Continuously be clear about the missions and objectives of the association you work, just like an individual from a gathering has a ton to do with your essential comprehension of the principal objective or the ‘master plan’.
- We should accept a guide to simplify it for your comprehension:
At the point when your 1 games player is functioning admirably together, you feel a deep satisfaction in their teamwork and comprehension of one another’s assets and shortcomings. Then again, when only one part is performing for him childishly, you will see the whole troop being angered, assuming you notice cautiously.

- Significant skills for the successful team manufacturer:
Advance the comprehension of why a gathering should be a gathering. It is pivotal that the arrangement of gathered people figures out their common objectives and furthermore that what every part independently contributes and carries to the gathering ought to be with a rationale of being a powerful team player as opposed to only a player.
Guaranteeing the team had sufficient information on their assignments. The individuals are expected to know all their singular obligations that are applicable to the all-encompassing objectives of the gathering. You could likewise complete team building projects to provide them with a little significance of what you are expecting out of them and how to build trust in a remote team. Working with viable communication is critical as the need might arise to be ok with one another to cooperate as an effective part. Team building requires team management of inner selves and requests and they should be prepared to set their singular acknowledgment aside for later and construct acknowledgment for the gathering overall all things being equal. There are various team management programs that you could sign up for. Building a gathering expects you to have the expertise of building areas of strength for a. Gain proficiency with the specialty of knowing individuals as it could lead you up the achievement stepping stool where you will be expected to deal with teams at large.
