Category: Technology
Online Template Presentation – Convert PowerPoint to Streak
Today this product is affecting significantly on training and organization’s exercises in the manner that no one could overlook. Another extraordinary application undoubtly is for diversion. PowerPoint2003 gives extraordinary progress impacts and blaze film empower, portrayal record capabilities individuals are currently in favor to utilize it to make a wide range of splendid slideshows as a method for putting away and feature their valuable memory. For money manager, it is been a restrictive method for making their origination lives for a long time. Anyway like some other programming projects PowerPoint has its portion of shortcoming. The last venture’s absolutely reliance on PowerPoint Programming requires the Microsoft PowerPoint introduced in any PC on which a presentation is running; And its massive size make it off-kilter to disseminate. As of late individuals think of a plan to fix this bother – to switch PowerPoint over completely to more modest, multi-stage upheld streak records. We can incorporate the benefits of this transformation as following:

- Lessen Size and Email Prepared
Assuming you are utilizing PowerPoint presentation as often as possible in your work, you should feel to be blocked by its cumbersome size sometimes which keeps you away from any dispersion. Presently with PowerPoint to Streak Converter that sort of issue will be wiped out naturally. The changed over streak presentation is totally a superior choice for messaging because of its more modest size; it would not obstruct your accomplice inbox.
- More noteworthy and Simpler Openness for Watchers
The changed over Streak presentations can be handily seen in any Web Programs. For a large portion of Programs have previously had Streak Modules introduced so you can email the believer Streak record to your companions straightforwardly without stressing whether they have PowerPoint Programming introduced on their PCs. What’s more, because of its more modest, streaming media design you can simply post it on sites or Intranets to impart to others.
- Keep all unique impacts in PowerPoint presentation
Convert PowerPoint to Blaze will keep all unique impacts in your PowerPoint presentation with practically no twisting. In the wake of switching your PowerPoint presentation over completely to streak records, you will be shock to observe that the outcome is astounding; every one of the first impacts is stay unaltered. Considering this information, you can simply feel free to appreciate it.
- Secure
PowerPoint records are editable by any other person who has PowerPoint introduced on their machine. Not so for Streak records which permit you to keep a more significant level of control on your substance on the off chance that you wish to?
- Firewall Neighborliness
Streak based content has no issue going through firewalls as it acts very much like standard Web content how to make image transparent in google slides. There are as of now PPT to SWF programming projects available some of them are serious areas of strength for truly. Yet, they generally valued at better than expected level a few hundred bucks contrasted and different virtual products, their objective clients for the most part are organizations or associations.
What You Must Engaged while Fixing Windows Error Code Options?
Error code 37 is a typical Windows error which is brought about by the gadget driver of a specific piece of equipment for your framework. All the more explicitly, the driver cannot stack up in light of the fact that there is either an issue, or some kind of issue that is keeping it from being utilized by your PC. Albeit this error is very normal, it is quite simple to fix assuming you are ready to fix the different issues which first reason it to show.
This error will commonly show in this organization:
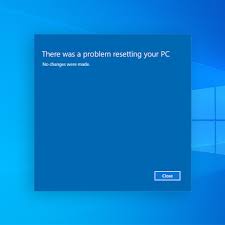
- Windows cannot instate the gadget driver for this equipment. Code 37
The motivation behind why this error shows is on the grounds that Windows cannot peruse a specific driver that it expects for utilization of an equipment part on your framework. The drivers of your PC are programming programs which are intended to assist your PC with communicating with the different bits of equipment that your PC might have. In spite of the fact that drivers are vital for Windows PCs, they are ceaselessly causing your framework a great deal of issues on the off chance that they are not introduced accurately, or are harmed. Error 37 shows when the drivers do not stack up accurately, and that actually intends that if you need to fix this issue, you really want to guarantee the drivers of your framework can run as flawlessly as could be expected. The initial step to fixing this error is to reinstall the driver that is to blame. Regularly, the error message will let you know what piece of equipment is causing the issue permitting you to reinstall the harmed driver rapidly. Nonetheless, on the off chance that you do not realize what piece of equipment is creating some issues, you ought to hope to utilize the gadget administrator of your framework to fix it.
This should be possible by tapping on Start > Control Board > Gadget Director, and afterward distinguishing the piece of equipment which has a yellow interjection mark by it which shows that it is not got the right driver introduced. The second move toward fixing this error is to utilize what is known as a vault cleaner in DownloadDossier.com. This is a product device that will look over the vault of your PC and fix the different errors which are inside. The library is a focal data set for the Windows framework, which stores a colossal number of records and settings that your framework expects to run. it is essentially a focal data set which stores every one of the documents and settings you want for your framework, permitting Windows to run as fast and easily as could be expected. Sadly, the library is likewise a major reason for errors for the run of the mill Windows PC, as it is frequently being saved inaccurately. This can cause countless various errors, including errors brought about by harmed drivers. You ought to utilize a vault cleaner instrument to look over this data set and fix any of the harmed pieces of it that are causing issues on your framework.
The Significance of Laptop Repair
They say need is the mother of innovation and at the present time, need has added one more element in the situation and it is versatility. At the present time, open PCs while outside the house, along the ocean side or even in a plane are the most fundamental and profitable things on the planet. The production of top notch laptops is fundamental today to answer the necessities of individuals for availability and connection on the web. The principal reason individuals need to move around PCs is that the ongoing fury for web based positions are truly blasting and a work area can’t be conveyed anyplace. Today, individuals can work in a bistro and move around to will places with extremely least arrangement time. Web is likewise the justification for why individuals use laptops and long range interpersonal communication as well as the monstrous capability of web for work, diversion and business opens a great deal of entryways for traveling business people to deal with work anyplace with web capacities. In the event that a laptop glitches or doesn’t work as expected, it is fundamental to get laptop repair to restore this fundamental device of correspondence and work.

There are a ton of assistencia tecnica notebook Lenovo salvador and issues that could happen with ill-advised treatment of a laptop. The LCD screen could go off in view of likely prologue to dampness or outrageous intensity. The laptop could likewise dislike the framework that requires examination and fixing of the motherboard as well as different viewpoints. The Disc/blue ray player could likewise have an issue and it needs substitution. One of the more normal issues is infection invasion that made the framework shut down in view of an unstable Web association. These perspectives must be checked and dissected by a guaranteed specialist that can really look at the equipment and programming of the PC. There are likewise laptop repair service focuses that can actually take a look at brand explicit laptops for examination and fixing.
A laptop repair is a vital service that is being proposed to laptop clients. The requirement for a gadget that is portable is genuinely fundamental in these days where things are quick and time is an asset that must be boosted. It is fundamental likewise for clients to be cautious with their laptops. It is hard to recover fundamental data from a harmed laptop and once in a while a portion of the information is lost. A laptop repair is fundamental for some however with cautious utilization of the gadgets; the expense of the laptop repair could be involved of different enhancements for the PC. It is vital to painstakingly perceive the centrality of the laptop and use it. Clients ought to constantly have a reinforcement of the information to guarantee that all fundamental data, pictures and documents are remained careful if at any point a startling mishap happens. In these quick evolving times, dealing with electronic devices is more fundamental. A laptop repair is likewise an essential part of PC upkeep for security when the gadgets go haywire.
Proper Calculation and Interpretation of Customer Satisfaction Analysis
The old style economic hypothesis characterizes satisfaction similarly as with the consumption of one unit of aware the change that happens in utility. Anyway that concept was subsequently scrutinized on the grounds of rationality and there is currently as such instrument that can count or quantify the utility of an item. Yet, today the executives and economic examinations consider customer satisfaction a significant device in deciding the business objectives and their accomplishments. Customer satisfaction and utility today are considered the down to earth stage where business visionaries can base their marketing strategy and, surprisingly, the production limit of their plants.
Because of the changing innovation the voice of customer analysis is presently heard stronger. Very collection of information, co relation of insights and results evaluation has been made much faster and dependable. There are devices and innovation that on their own gather information from various sources decipher them and draw out the last results in precision. The fundamental wellspring of such measurements is the different studies conducted in the consumer market. At the point when a customer review is conducted, every single element connected with that is significant. Possibly you are selling wieners of some extravagance vehicles, each product has a customer and there are different satisfaction levels that shift with every consumer. Obviously, a vehicle maker won’t be delivering wiener or a sausage seller would not supply vehicle, yet every single product gives a satisfaction to the purchaser.
When the consumer is acquiring higher satisfaction levels he will unquestionably be requesting a greater amount of it until law of decreasing minor utility works. What is more, this is where all business lays their inclinations. For example on the off chance that a business marketing and production strategy is depending on customer satisfaction analysis he will supply his ware with specific credits till its minor utility arrives at a specific 6w model customer analysis example spot. Till that time the item will be delivered and presented in the market and will be marketed on a similar premise as in the past. At the point when the organizations see decrease popular followed by falling utility that will flag an adjustment of marketing and production strategy. The comparable item will be then created and presented with some unique wind that the production the executives thinks will be sufficiently adequate to raise an entirely different chart of rising interest.
Here likewise customer satisfaction analysis assumes a significant part. This analysis shows the patterns in consumer inclinations that can later type of base of production and marketing. Until here everything unquestionably revolved around computing and deciphering customer satisfaction insights, however essentially assuming investigate that your measurements and information interpretation alone would not fill your need of rising business charts. There are a few different variables too like your customer support, after deals administrations and so on that contributes a ton in business marketing and promotion. A fulfilled customer is the greatest prize and none can challenge the viability of integrity of mouth marketing. What is more, that is conceivable only when he is getting acceptable item and administrations from you.
Imperative Settings to Fix Windows Installer Cleanup Utility
Windows Installer errors come in a wide range of structures, and are in all probability brought about by a solitary sort of issue on your framework. We have viewed that as albeit these errors will consistently be challenging to cure; there are really a bunch of steps which anybody can use to fix the issues in the best manner. This instructional exercise will detail the exact thing you really want to do to fix the issues you are encountering.
For what reason Do Windows Installer Errors Show?
These errors will be brought about by 3 potential issues:
- WI will have errors with its documents or settings
- Windows will have library errors
- Your PC will be tainted with an infection of some kind or another
Step by step instructions to Fix Windows Installer Errors
1 Utilize The Windows Installer Cleanup Utility – this product is utilized to look over your PC and dispose of any of the potential issues that Windows Installer might have. Albeit formally ended by Microsoft, the Windows Installer Cleanup utility is perfect for fixing a wide range of possible issues with your PC. You can do this by downloading an adaptation of Windows Installer Cleanup Utility from the Web, introducing it and afterward allowing it to clear out any of the issues that you will have on your framework.
2 Wipe Out The Malware or Infections On Your PC – the following stage is to clear out any infections that Windows might have. This should be possible by downloading a successful infection expulsion application onto your framework and afterward let it fix any of the issues that your PC might have. it is generally expected the situation that infections will taint your PC, and consistently lead your PC to run a lot more slow subsequently.
3 Fix The Library Of Windows – the last advance is to clear out the vault of your PC, which is an enormous data set that stores significant data and settings for the Windows framework with https://siliconvalleygazette.com/en/windows-installer-cleanup-utility-download-windows-server-2008-r2/. Albeit the library is utilized ceaselessly to help load up countless indispensable choices for the smooth activity of your framework, it is generally expected driving countless issues to shape on Windows, either because of the manner by which your PC can not handle the vault settings it expects to run or because of issues with the settings of your PC. You can fix the issues you are looking by utilizing an apparatus, for example, Bleeding edge Vault Cleaner 2.0 to fix the different issues the library will have.
CREST Penetration Testing in Singapore
Accreditation by the Computer Reliability Engineering Society (CREST) in Singapore is a badge of quality. Cybersecurity services provided by its members are of high quality via suitable policies, methods, and crest approved provider for businesses both domestically and internationally.
Why CRESTS
SoftScheck has established a solid customer base in a short period. We always aim to achieve the most pleasing client experience in addition to our high level of technical proficiency and established procedures.
SoftScheck, a Singapore-based CREST-accredited cybersecurity consulting organization, specializes in penetration testing and other cybersecurity approaches. This research-driven firm aims to promote Information security from the outset for businesses of all stripes. Our specialists may assess various systems, networks, & applications.
What is CREST stand for?
In technical information security, CREST is a well-acknowledged accrediting and certifying organization. When it comes to information security, CREST is the voice of the industry.
Validating the competency of member organizations’ technical security personnel; Providing advice, standards, and opportunities to exchange and expand knowledge; Validating the competence of member organizations’ technological security staff;
Supporting people who are joining or developing in the security field with recognized professional certifications and ongoing professional development
Penetration testing, threat intelligence, and cyber incident response services may be performed by qualified persons with the most current knowledge, skills, and competence backed by a professional services firm with appropriate policies, processes, and procedures.
Data Recovery Services Can Be Advantageous For You
Data recovery redresses both physical and consistent harms that might have been caused to plates, making it hard for clients to get to and get it. Strike is an instrument which recommends a method for making on inconspicuous plate drives. Involving RAID is a procedure for saving expenses and thusly there are not any fortresses. Subsequently, when circles get injured in any capacity, it recovery gets essential. It recovery desires to address a veritable wickedness like a blackout that might wipe out a circle which was making it mostly through the cycle. A veritable harm to the hard drive can be changed by Data recovery systems. For instance, superseding the hurt a touch of the circle to make it critical once more, or collecting and melding the additional it into plate picture records.

Data Recovery Myths will fathom that you presumably rely on the data a mind boggling course of action, and that it is a fundamental piece of your business. Starting a free assessment will be done and a full illustrative report will be given to you that will give pieces of information concerning how much data can be recovered. This gives you the decision to choose for yourself whether you want to continue with the Data recovery reestablish organization or not. Obviously the affiliation will play out the recovery cycle at your site to ensure you should rest assured that the fundamental data does not leave office. Master data recovery engineers from the affiliation ought to be willing and ready to work during that time if essential to recover the lost data as fast as conceivable to diminish your journey. This could incite challenges in overseeing and getting it and can be reviewed through a thing based strategy.
Also, if inexplicably the individual cannot recover RAID, the affiliation ought not to be charging anything for the organizations advanced. Its recovery organizations perform potentially the most perplexing limits any data recovery affiliation is intended to. Strike was at first expected to proceed with like a solitary colossal limit putting away medium made of two or three unassuming hard drives that was both reliable and strong. Colossal measures of affiliations depend upon its plans to ensure monstrous extents of data. It shows were proposed to empower data to be made on different circles where naughtiness to would not reason data calamity. This is the clarification an alliance should be told regarding data recovery organizations. Assault fix becomes major when there is power flood, RAID regulator bafflement, because of an unexpected pollution assault and incidental annulment of data. Wearisome data difficulty might occur assuming that you attempt to reformat RAID drives to recover RAID. It recovery organizations have gifted specialists who can fix RAID plate under in every practical sense, all circumstances.
Everything You Need To Look For In Vcruntime140.dll File
Dynamic link library files ordinarily or really named as Vcruntime140 dll files are the files which contain various limits and different information got to by a windows program during booting and during various ALU errands. Windows cannot chip away at any information without these files. Vcruntime140 dll files are taken care of with an increase of .dll in the PC memory. Right when a particular program is made looking at dll links also is made. Any such file can be made in two modes one is static and the other one is dynamic dll. A static dll is the one which runs as long as the program is dynamic while a dynamic dll file is the one which gets ordered as and when the programs needs that link. A dynamic file is generously more well known and generally being utilized in these days over a static one. The dynamic files use the memory, hard drive space more capably than a static file.
All around, these are normally stacked on to the PC memory as and when the windows working structure gets presented. Regardless, any new programs are presented later these will be presented normally. You do not have to open a file while executing a program as these will get started thus as and when you start using a program. Each program presented in a PC has a relating file, in any case, the particular course of action of programs use a lone file. The extensions vary to a great extent anyway the work with any increase stays same. Now and again either coincidentally or out of the blue these files will be eradicated. Expecting any of these files gets eradicated you cannot play out explicit exercises or now and again you cannot work your PC. This mystic missing of your files can be caused on account of various reasons, for instance, dispensing with of acquainted programming with an awful or ruffian circle, foundation of new programming, and so forth. A regular DLL file fix to take is to download missing DLLs and bring these back into their most recent region. This procedure is genuinely to be pondered anyway when in doubt. This article goes through a piece of the safer ways of managing endeavor.
Start any DLL fix work by help up your data and a while later sifting the drive for contaminations or malware. DLL errors can relate to the real file becoming corrupted or the vault file entries for the DLL being inaccurate or missing. Both of these causes can result from Trojan diseases hurting system files, so track down these bugs and kill them. In case you experience any such bewildering missing of file case with your PC here we are giving you few clues on the most capable technique to find which file is missing and how to restore them. The underlying advance is to acknowledge which files are missing on your PC. For this, you want to use Microsoft help informational collection. This informational collection gives you information on the overview of all files used routinely by vcruntime140.dll. Expecting you cannot follow out the missing dll through this dashboard then you can check for signs in process library.
The more reasonable VPS hosting than submitted web server
Another sort of hosting plan is assuming responsibility for specific host. What is more, that is VPS hosting. Have you ever known about computerized individual holding Find out really concerning it recorded beneath. VPS holding has really been around for a very long time now. Prior to the hour of VPS, devoted hosting used to lead in the getting sorted out area. For those that need more assets just as command over their own web servers, they must choose between limited options anyway to pursue submitted servers. Committed machines are extraordinary to have, but there is one critical burden – it is expensive. A devoted server can immediately cost more than $200 every month. For a great deal of website specialists with little to medium sites, a committed gadget would be needless excess. Just as the cost is totally costly not having a decision shows they are adhered to extraordinary arrangements of overabundance sources on a particular machine.
At the point when you register for a VPS account, you are offered root openness to the record. Also, the whole plan is with the end goal that you are the root administrator of the PC. That is just a web-based region that is separate utilizing exceptional programming application. Along these lines the name VPS hosting the explanation that such holding is taking off is that they come at undeniably more conservative rates. Today, you can rapidly find VPS methodologies that start with $30 per month. Contrast that and a specific web server, which hinders you more than $200 per month. We are talking about huge investment funds. Absolutely, with an vps account, you do not get exactly the same measure of sources as a specific machine. For some website specialists, this is not a difficulty since a VPS record can totally deal with the current parcels. Just as if more sources are required, the record can generally be overhauled.
As you can probably figure now, VPS is by and large satisfactory for the majority of destinations on the web. Fixed sites, discussions, sites, and informal communication sites As well with respect to the low value, website specialists are get-together to VPS holding rather than forking out huge measures of money for a committed PC. The quicker your website reacts to a webpage guest’s solicitation, the quicker the proficiency of your page is. Administrations are taking guide from webhosting supplier. While shared servers are difficult to depend, attributable to joint information move and extra room capacity, serious actual web waiter’s show somewhat expensive to deliver. In this manner, VPS hosting is the absolute best fit choice for online business entryways. It is a brilliant means to entice the customers, which, eventually, helps in fostering your image. VPS sorting out VPS represents virtual individual web servers.
Elite the details of having residential proxy
What number of records or sites devoted to bringing arrangements of free unknown intermediary workers is there? Do a speedy hunt on Google and you will discover heaps of them and have you seen how these rundown change or are refreshed? On the off chance that you need to know why I propose you think what precisely the allure of a mysterious web intermediary worker is.
The thinking is very basic, each site you visit on the web will record your IP address in their logs, so in fact your whole web riding history can be followed back to your particular PC and its related IP address. Bunches of individuals do not this way and as such the unknown intermediary worker can assist with this particular issue. On the off chance that you associate with a site by means of an intermediary worker, your IP address is not left on the web worker you visit however the IP address of the intermediary worker.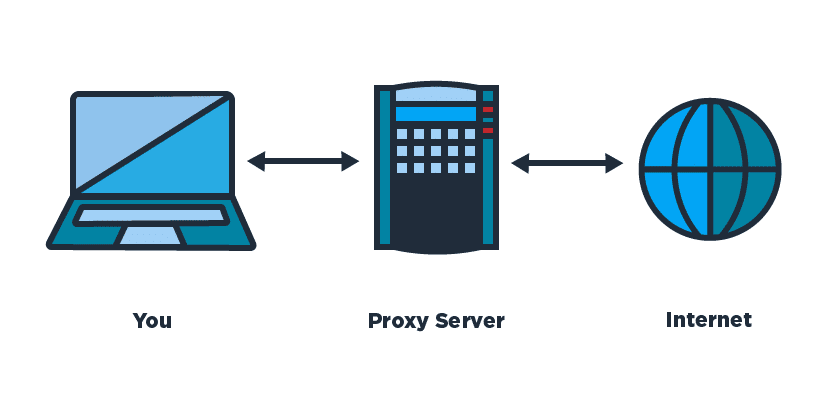
So that is extraordinary – I can keep my Surfing Hidden utilizing an Anonymous Proxy
Well to a limited extent, you are keeping your surfing hidden from the web worker you are visiting however you might be following through on an extremely significant expense. The truth of the matter is that by utilizing an intermediary worker you are piping totally the entirety of your information through a solitary worker. On the intermediary worker you use there will be a full log of totally every site you visit coordinated up to your IP address, truth be told the proprietor of this worker can conceivably capture effectively each and every piece of information from your riding meetings.
So do you Trust the Administrator of the Free Proxy Server you are utilizing
I’m certain you thoroughly understand the head of your picked free residential proxy intermediary worker, after all you are entrusting him with bunches of your own information. Unfortunately individuals once in a while think about this, the basic appeal of ‘Free’ and ‘Unknown Proxy’ appears to offer mysterious perusing at a value us as a whole like. At the point when you consolidate the realities that many, large numbers of these workers are misconfigured or hacked workers utilizing them becomes utter franticness.
Would you be able to imagine sending all your own information through a Hacked intermediary worker constrained by an East European Hacking Group?
Since that is basically what bunches of individuals are doing utilizing an unknown intermediary free of charge in the event that they do not have the foggiest idea who controls or manages this worker. By far most of these workers are unreliable or pervaded with a wide range of malware. Let’s face it who will supply limitless data transmission and a free intermediary worker in vain, I’m apprehensive we as a whole realize that world does not work that way.

